Showing posts with label beef. Show all posts
Showing posts with label beef. Show all posts
Tuesday, June 13, 2017
Kali Linux Tutorial Hack Your Own Network and Beef Up Its Security
Kali Linux Tutorial Hack Your Own Network and Beef Up Its Security

Kali Linux is packed with a ton of software for testing security holes in your network. There are far too many to list here, but were so enamored with it that we decided to pick a few of our favorite tools and show how they work: Aircrack, Airbase, and ARPspoof. Well show you how to crack a Wi-Fi password with brute force techniques, create a fake router to trick machines into logging into it, and perform a man in the middle attack to eavesdrop on network communications. Remember: use these powers for good, not for evil. Knowing how to do these things can get you out of a jam or help you learn to secure your own network, but doing them to someone else is not something we recommend.
Read my previous article to know more about Kali Linux: An Introduction To Hacker’s OS: Kali Linux And Setup Tutorial.
Crack a WPA Wi-Fi Password with Aircrack

Kali Linux comes with a whole suite of apps for cracking Wi-Fi networks, including Aircrack and Reaver—both of which weve mentioned before for cracking WEP and WPA passwords, respectively.
Recommend to read: How To Hack Wi-Fi WPA/WPA2 With Kali Linux
However, WEP passwords arent that popular anymore (because theyre so easy to crack), and Reaver only works if a network has WPS enabled. So today, were going take another look at Aircrack and use it to to brute force our way into a WPA network (with the help of a password list).
Step One: Configure Your Wireless Card

First things first: disconnect from all wireless networks. Then open up terminal. In order to use Aircrack, youll need a wireless card that supports injections. Type this into the Terminal to make sure your card supports it:
airmon-ngThis lists all the wireless cards that support this crack. If you card doesnt support injections, it wont show up here. Yours is likely listed under interface as wlan0, but it may depend on your machine.
Next, type in:
airmon-ng start wlan0Replace
wlan0 with your cards interface address. You should get a message back saying that monitor mode was enabled.Step Two: Monitor Your Network

Next, youre going to get a list of all the networks in your area and monitor yours.
Type in:
airodump-ng mon0Youll see all the networks in your area. Locate your network from the list, and copy the BSSID, while making a note of the channel its on. Tap Ctrl+C to stop the process.
Next, type this in, replacing the information in parentheses with the information you gathered above:
airodump-ng -c (channel) --bssid (bssid) -w /root/Desktop/ (monitor interface)It should read something like this:
airodump-ng -c 6 --bssid 04:1E:64:98:96:AB -w /root/Desktop/ mon0Now, youll be monitoring your network. You should see four files pop up on the desktop. Dont worry about those now; youll need one of them later. The next step is a bit of a waiting game, as youll be sitting around waiting for a device to connect to a network. In this case, just open up a device you own and connect to your Wi-Fi. You should see it pop up as a new station. Make a note of the station number, because youll need that in the next step.
Step Three: Capture a Handshake

Now, youre going to force a reconnect so you can capture the handshake between the computer and the router. Leave Airodump running and open up a new tab in Terminal. Then type in:
aireplay-ng -0 2 -a (router bssid) -c (client station number) mon0It should look something like:
aireplay-ng -0 2 -a 04:1E:64:98:96:AB -c 54:4E:85:46:78:EA mon0Youll now see Aireplay send packets to your computer to force a reconnect. Hop back over to the Airodump tab and youll see a new number listed after WPA Handshake. If thats there, youve successfully grabbed the handshake and you can start cracking the password.
Step Four: Crack the Password

You now have the routers password in encrypted form, but you still need to actually figure out what it is. To do this, youll use a password list to try and brute force your way into the network. You can find these lists online, but Kali Linux includes a few small lists to get you started in the /usr/share/wordlists directory, so well just use one of those. To start cracking the password type this in:
aircrack-ng -a2 -b (router bssid) -w (path to wordlist) /Root/Desktop/*.capSo, continuing with our above example and using one of the built-in wordlists, it should read something like:
aircrack-ng -a2 -b 04:1E:64:98:96:AB -w /usr/share/wordlists/fern-wifi/common.txt /Root/Desktop/*.capNow, Aircrack will try all of those passwords to see if one fits. If it does, youll get a message saying the key was found with the password. If not, give another one of the password lists a try until you find one that works. The bigger the password list, the longer this process will take, but the greater chance you have of succeeding.
How to Use This Information to Stay Safe
So, you just brute forced your way into your own network. Depending on how good your password is, it either took you five minutes or five hours. If your password is something simple, like "password123", then chances are one of the smaller wordlists was able to crack it pretty quickly. If it was more complicated, it probably took a long time or never surfaced the password at all (if so: good for you!).
The best protection here is a good, strong password on your router. The longer, weirder, and more complex it is, the better. Likewise, make sure youre using the WPA2 security protocol and you dont have WPS enabled.
Create a Fake Network with Airbase

Next up, lets take a look at how you can spoof a network address to trick people into signing into the wrong network so you can watch what theyre doing. Hackers might do this so you sign into the fake network thinking its your real one, then performing a man in the middle attack (more on that in the next section) to gather information about you from your traffic. This is amazingly easy to do with a tool in Kali Linux called Airbase.
Essentially, youll turn your Wi-Fi adapter on Kali Linux into an access point with the same name as another network. In order to do this, youll follow the same line of research as you did above, but the endings a bit different.
Step One: Configure Your Wireless Card
Just like last time, you need to set up your wireless card to monitor traffic. Open up Terminal and type:
airmon-ngThis lists all the wireless cards that support this crack. Yours is likely listed under interface as wlan0.
Next, type in:
airmon-ng start wlan0Now youre in monitor mode. Its time to find the network you want to spoof.
Step Two: Find a Wi-Fi Network to Spoof

In order to spoof a router, youll need some information about it. So, type in:
airodump-ng mon0Available link for download
Read more »
Tuesday, February 21, 2017
Kali Linux Tutorial Hack A Web Browser Using BeEF
Kali Linux Tutorial Hack A Web Browser Using BeEF

Step 1: Start Cooking BeEF
BeEF is built into Kali Linux, and it can be started as a service and accessed via a web browser on your localhost.
Here is a complete tutorial about hackers OS Kali Linux, so read this before you go ahead: An Introduction To Hacker’s OS: Kali Linux Setup Tutorial
So let’s start by firing up Kali and cooking a bit of BeEF. Start the BeEF service by going to “Applications” -> “Kali Linux” -> “System Services” -> “BeEF” -> “beef start.”

Step 2: Opening a Browser to BeEF
The BeEF server can be accessed via any browser on our localhost (127.0.0.1) web server at port 3000. To access its authentication page, go to:
http://localhost:3000/ui/authentication
The default credentials are “beef” for both username and password.

Great! Now you have successfully logged into BeEF and are ready to begin using this powerful platform to hack web browsers.
Note that in the screenshot below that my local browser, 127.0.0.1, appears in the left hand “Hooked Browsers” explorer after I clicked on the link to the demo page. BeEF also displays its “Getting Started” window to the right.
Note that in the screenshot below that my local browser, 127.0.0.1, appears in the left hand “Hooked Browsers” explorer after I clicked on the link to the demo page. BeEF also displays its “Getting Started” window to the right.
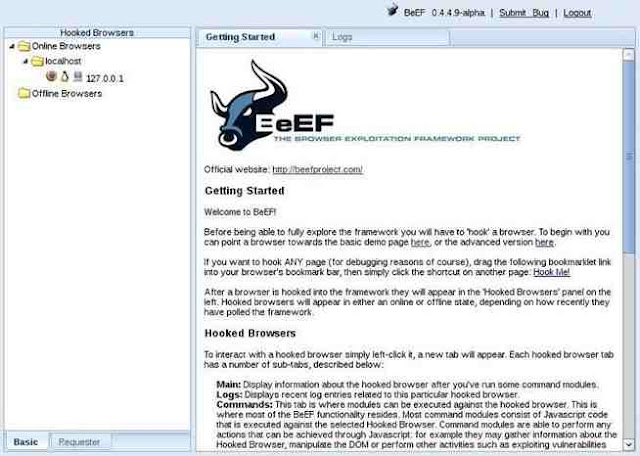
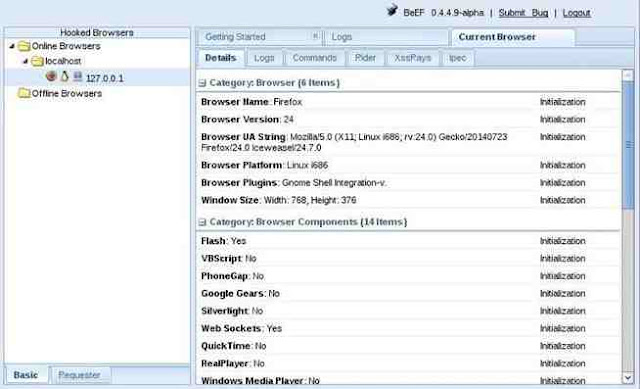
Step 3: Viewing Browser Details
If I click on the local browser, it will provide with more choices to the right including a “Details” window where we can get all the particulars of that browser. Since I am using the Iceweasel browser built into Kali, which is built upon Firefox, it shows me that the browser is Firefox.
It also shows me the version number (24), the platform (Linux i686), any components (Flash, web sockets, etc.), and more information that we will be able to use in later web application hacks.
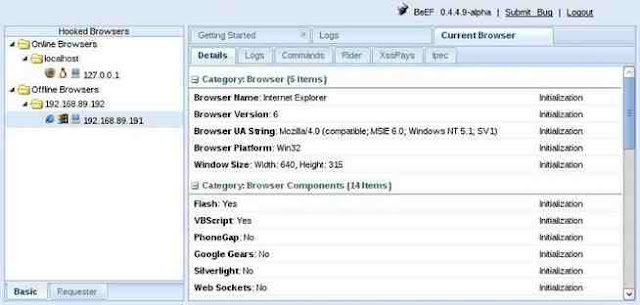
Step 4: Hooking a Browser
The key to success with BeEF is to “hook” a browser. This basically means that we need the victim to visit a vulnerable web app. This injected code in the “hooked” browser then responds to commands from the BeEF server. From there, we can do a number of malicious things on the victim’s computer.
BeEF has a JavaScript file called “hook.js,” and if we can get the victim to execute it in a vulnerable web app, we will hook their browser! In future tutorials, we will look at multiple ways to get the victim’s browser hooked.
In the screenshot below, I have “hooked” an Internet Explorer 6 browser on an old Windows XP on my LAN at IP 192.168.89.191.
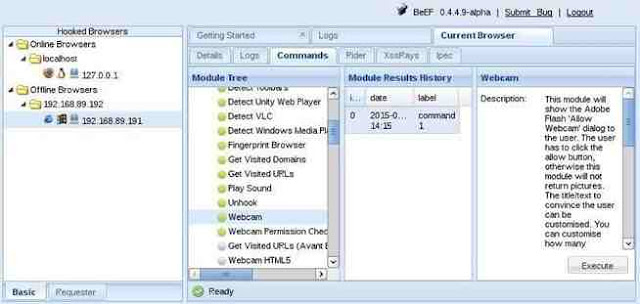
Step 5: Running Commands in the Browser
Now, that we have hooked the victim’s browser, we can use numerous built-in commands that can executed from the victim’s browser. Below are just a few examples; there are many others.
- Get Visited Domains
- Get Visited URLs
- Webcam
- Get All Cookies
- Grab Google Contacts
- Screenshot
In the screenshot below, I selected the “Webcam” command that many of you may be interested in. As you can see, when I execute this command, an Adobe Flash dialog box will pop up on the screen of the user asking, “Allow Webcam?” If they click “Allow,” it will begin to return pictures from the victim’s machine to you.
Of course, the text can be customized, so be imaginative. For instance, you could customize the button to say “You have just won the lottery! Click here to collect your winnings!” or “Your software is out of date. Click here to update and keep your computer secure.” Other such messages might entice the victim to click on the box.
Step 6: Getting Cookies
Once we have the browser hooked, there is almost unlimited possibilities of what we can do. If we wanted the cookies of the victim, we can go to “Chrome Extensions” and select “Get All Cookies” as shown in the screenshot below.

When we click on the “Execute” button to the bottom right, it will begin collecting all the cookies from the browser. Obviously, once you have the user’s cookies, you are likely to have access to their websites as well.
BeEF is an extraordinary and powerful tool for exploiting web browsers. In addition to what I have shown you here, it can also be used to leverage operating system attacks. We will be using it and other tools in my new series on hacking web applications, mobile devices, and Facebook, so keep coming back, my greenhorn hackers.
Recommended Articles To Become A Hacker:
How To Become A Hacker - Basic Guide For Beginners 2015
Understand The Hacker Mindset To Become A Real Hacker
Programming Languages For Hackers And Learn It From Most 6 Helpful Websites
Installing Hackers OS Kali Linux In VMware (Beginners Guide With Screenshots)
Easy Steps to Create Web Penetration Testing Lab in Kali Linux
Introduction to using Metasploit in Kali Linux
An Introduction To Hacker’s OS: Kali Linux And Setup Tutorial.
Linux Powerful Distros For Hacking Or Security: Kali, Tails And Qubes
Become A Hacker: What Is Denial of Service (DoS) Attack?
Available link for download
Subscribe to:
Posts (Atom)