Showing posts with label web. Show all posts
Showing posts with label web. Show all posts
Saturday, July 8, 2017
Key Vulnerabilities in Corporate Information Systems in 2014 Web Applications Passwords and Employees
Key Vulnerabilities in Corporate Information Systems in 2014 Web Applications Passwords and Employees

From 2013 to 2014, there was an increase in the vulnerability of the information systems of large enterprises. In about 60% of system attacks, the network perimeters were penetrated via web application vulnerabilities. Additionally in 2014, there was decreased awareness among employees regarding security issues, as they were more likely to follow unverified links and open files attached to e-mails from unknown sources.
These findings are outlined in detail in Positive Technologies’ 2014 penetration testing results publication and contrast significantly from the 2013 findings. The penetration testing simulates a hacker attack and provides a more realistic assessment than traditional auditing techniques alone.
General Results
The penetration testing data used in this article is drawn from testing the information systems of 18 large public and private companies. The firms are comprised of Fortune Global 500 firms and include some of the largest Russian firms in terms of volume of products produced annually, as ranked by Expert RA. More than half of the enterprises had multiple international subsidiaries and most systems had hundreds of active hosts available at the network perimeter. The majority of the firms operate in the manufacturing, banking and IT sectors.
In 2014, 94% of systems in the penetration testing study contained vulnerabilities that allowed testers to gain full control over some critical resources — Active Directory, ERP, e-mail, or network equipment control systems. In 67% of cases, an external attacker could gain full control over the most critical resources and in 27% of cases gaining access to the intranet user segment was enough to facilitate full control over the critical resource.
In both 2013 and 2014, almost all the systems had high-severity vulnerabilities and most of these critical vulnerabilities related to configuration flaws. However in 2014, most systems, 78%, had critical vulnerabilities related to outdated software updates, worse than the 2013 results of about 50%. The average age of the most outdated patch was 73 months, compared to just 32 months in 2013. In three systems, MS08-067 (CVE-2008-4250), a 6-year-old critical vulnerability widely used by both hackers and the Conficker network worm, was still in use.

System compared by maximum severity of vulnerabilities caused by the lack of updates
Additionally in 2014, almost every information system, 89%, had vulnerabilities related to web application code errors and more than half of the companies, 61%, had high-severity vulnerabilities.
Security Perimeter Flaws
In 73% of systems, an outside attacker accessing the network from the Internet could access intranet hosts without using social engineering. When combining the use of intranet hosts with social engineering outside access to the system was gained in 87% of cases. In 2014, a low-qualified attacker could successfully attack 61% of systems, compared to just 46% in 2013.

Difficulty of penetrating the perimeter
Penetrating the perimeter in 2014, as in 2013, required exploitation of, on average, only two vulnerabilities However, one vulnerability was enough to penetrate more than half of the systems (6 out of 11) in 2014. Additionally, in 60% of all cases the penetration vector is based on web application code vulnerabilities. For example, SQL Injection appears in 67% of systems, and unrestricted file upload in 40%.
The most common vulnerabilities at the network perimeter are:
- Network equipment and server control interfaces available from the Internet, rising from 82% to 93% from 2013 to 2014.
- Dictionary passwords, including default and empty passwords — 87%. Also note that 67% of all systems used dictionary IDs and passwords as administrator IDs and passwords at the perimeter. Both of these factors increase the likelihood that an attacked could access the intranet.
By contrast, Heartbleed and Shellshock vulnerabilities, both of which garnered media scrutiny in 2014, have not been widely used in hacks, as the coverage encouraged most large companies to install updates to protect against them. Nevertheless, one company in this study did have an unfixed Heartbleed vulnerability that allowed attackers to obtain many customers’ credentials.

The most common vulnerabilities at the network perimeter
Gaining access to the company intranet is often the first step for an external attacker to gain access to critical resources. The 2014 report demonstrates that after gaining full control over critical resources in 80% of systems, the hacker would have been able to penetrate the network perimeter.

Privilege level gained by external attacker
Intranet Security Flaws
Positive Technologies also considered the attack vectors of an internal hacker. The results of a hack by an employee located in the user segment of the network resulted in unauthorized access privileges leading to full control over information infrastructure in 78% of cases and access to critical resources such as banking and ERP systems in all the cases.
In 56% of cases, a low skilled attacker is able to access critical resources. Complicated attacks, requiring a high skill level to coordinate, were not necessary to access critical resources in 2014. By contrast, in 2013 they were required to penetrate 17% of systems. On average, an internal attacker needed to exploit three different vulnerabilities to gain control over critical resources in 2014, worse than the 2013 results in which an attacker had to exploit an average of five vulnerabilities.

Difficulty of gaining access to critical recourses by internal attackers
Weak passwords are still the most common intranet security vulnerability detected in all the systems studied. Every system had weak administrator passwords, more than half of them were only six characters long.

Systems compared by dictionary passwords. Administrator passwords are red, user passwords are blue
The second most common intranet vulnerability is insufficient security on privileged accounts, a problem found in 88% of systems in 2014. In the case of the privileged accounts attack, the hacker can use high privileges to access the domain on behalf of an unknown account due to architecture flaws in the Kerberos protocol, an attack that is hard to detect.

The most common intranet vulnerabilities
Lack of Staff Awareness
As part of the penetration testing IS awareness checks were carried out among the system users. The results were based on the most common hacker methods — emailing messages containing an attachment or with a link embedded. The penetration testing monitored the number of links opened and files downloaded, as well as the number of credentials entered, to simulate a phishing scam.
From 2013 to 2014, staff vigilance about these types of attacks decreased significantly. In 2014, staff at 67% of companies whose systems were tested showed low or extremely low awareness level, and the others were estimated as "below average". In particular, the number of users who followed the link increased from 11% to 20% and those who entered credentials in the phishing simulation quadrupled to 15%.

The threat events, total number of messages
The results of the penetration testing presented in this article argue for improved security measures. Key areas include password policy, web application security, regular security updates, and privileged account security and user awareness. Additionally regular security audits of information systems and penetration testing both internal and external are recommended.
To access the full report please see: www.ptsecurity.com/upload/ptcom/PT_Pentalytic_2015_ENG.PDF
Available link for download
Labels:
2014,
and,
applications,
corporate,
employees,
in,
information,
key,
passwords,
systems,
vulnerabilities,
web
Saturday, April 29, 2017
Kellton Tech Solutions walk in for Web HTML Developer
Kellton Tech Solutions walk in for Web HTML Developer

Company :Kellton Tech Solutions
Website :www.kelltontech.com
Job Role :Web/HTML Developer
Eligibility :Any Graduate
Experience :2 - 6 Years
Salary :Rs: 2,00,000 - 6,00,000 P.A
Job Location :Gurgaon
Walk-In Date :03 Jan - 06 Jan 2017
Walk-In Time :11:00 AM - 04:30 PM
Company Profile:
Kellton Tech is a full-grown software development company, offering end-to-end IT solutions, strategic technology consulting and product development services in Web, SMAC (Social, Mobile, Analytics, Cloud), ERP-BPM, and IoT space. The company is listed on India?s largest stock exchange BSE and NSE [Code: KELLTONTEC; BOM: 519602] and is ISO 9001:2008 and CMMI Level 3 certified. Our methodology of inventing infinite possibilities with technology helps us develop best in-class and cost effective solutions for our clients.
Founded in 1993, we have since grown by leaps and bounds and now have over 200 clients ranging from start-ups to early stage, enterprises, and Fortune 1000 companies. Using our flagship product, KLGAME? (Kellton Tech Location based Gamification, Analytics and rich Messaging Engine), we have helped clients across the globe think disruptively about their business in a cost effective manner.
Job Description:
- Should have experience on converting PSD to XHTML.
- Should have strong knowledge on XHTML, CSS, JavaScript, Photoshop, Drupal.
- Should be well versed with the behavior of different browsers available like IE, Firefox, Opera, Safari, Google Chrome, MAC and Linux browsers.
- Should have strong knowledge of JavaScript, Jquery.
- Knowledge of XHTML and CSS; intermediate experience in JavaScript/DHTML/Ajax, XML/XSLT, JavaScript, Jquery, Drupal.
- Pixel-perfect attention to detail.
- Familiar with many content management.
- A flexible attitude with proven experience of working in a team.
- Excellent communication skills and attention to detail.
- Awareness and ability to analyze performance and communicate analysis while presenting.
- Good communication skills.
How to Apply:
Interested candidates can send their resumes to Disha.nautiyal@kelltontech.com :
Total Experience:
R.Exp into MVC:
Cctc:
Ectc:
Current Location:
Joining Time:
or
Interested candidates can directly walk-in to the mentioned address.
Venue Details:
Kellton Tech Solutions Ltd.,
Plot No. 270, Udyog Vihar,
Phase - 2, Next to DHL Building,
Gurgaon 122016.
Contact Details:
Disha
0124-4698912
 To know job updates in FaceBook
To know job updates in FaceBookFaceBook Group Facebook Page
Available link for download
Thursday, April 20, 2017
Kung Fu Panda 3 2016 720p BlueRay WEB DL x264 Dual Audio
Kung Fu Panda 3 2016 720p BlueRay WEB DL x264 Dual Audio
?Released On: 29 Jan 2016
?Genre/Tags: Animation, Action, Adventure
?Star Cast: Jack Black, Bryan Cranston, Dustin Hoffman, Angelina Jolie
?Director: Alessandro Carloni, Jennifer Yuh Nelson
?Storyline: When Po’s long-lost panda father suddenly reappears, the reunited duo travels to a secret panda paradise to meet scores of hilarious new panda characters. But when the supernatural villain Kai begins to sweep across China defeating all the kung fu masters, Po must do the impossible-learn to train a village full of his fun-loving, clumsy brethren to become the ultimate band of Kung Fu Pandas.
?Download Now
?Screen Shots :




Available link for download
Tuesday, February 21, 2017
Kali Linux Tutorial Hack A Web Browser Using BeEF
Kali Linux Tutorial Hack A Web Browser Using BeEF

Step 1: Start Cooking BeEF
BeEF is built into Kali Linux, and it can be started as a service and accessed via a web browser on your localhost.
Here is a complete tutorial about hackers OS Kali Linux, so read this before you go ahead: An Introduction To Hacker’s OS: Kali Linux Setup Tutorial
So let’s start by firing up Kali and cooking a bit of BeEF. Start the BeEF service by going to “Applications” -> “Kali Linux” -> “System Services” -> “BeEF” -> “beef start.”

Step 2: Opening a Browser to BeEF
The BeEF server can be accessed via any browser on our localhost (127.0.0.1) web server at port 3000. To access its authentication page, go to:
http://localhost:3000/ui/authentication
The default credentials are “beef” for both username and password.

Great! Now you have successfully logged into BeEF and are ready to begin using this powerful platform to hack web browsers.
Note that in the screenshot below that my local browser, 127.0.0.1, appears in the left hand “Hooked Browsers” explorer after I clicked on the link to the demo page. BeEF also displays its “Getting Started” window to the right.
Note that in the screenshot below that my local browser, 127.0.0.1, appears in the left hand “Hooked Browsers” explorer after I clicked on the link to the demo page. BeEF also displays its “Getting Started” window to the right.
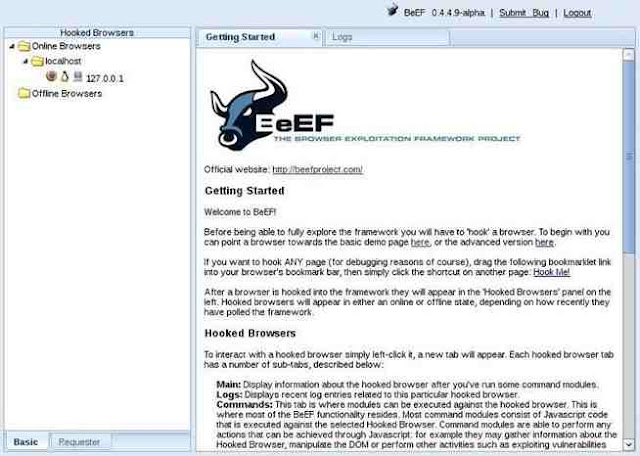
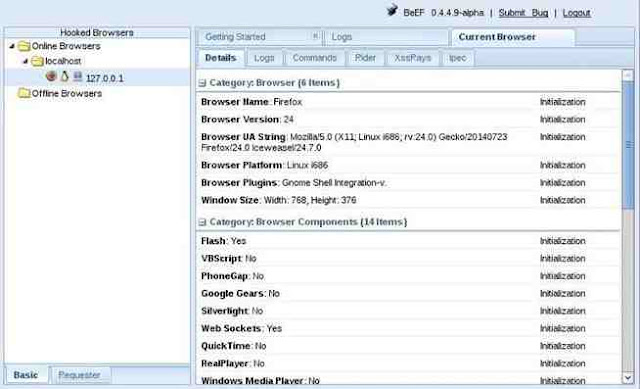
Step 3: Viewing Browser Details
If I click on the local browser, it will provide with more choices to the right including a “Details” window where we can get all the particulars of that browser. Since I am using the Iceweasel browser built into Kali, which is built upon Firefox, it shows me that the browser is Firefox.
It also shows me the version number (24), the platform (Linux i686), any components (Flash, web sockets, etc.), and more information that we will be able to use in later web application hacks.
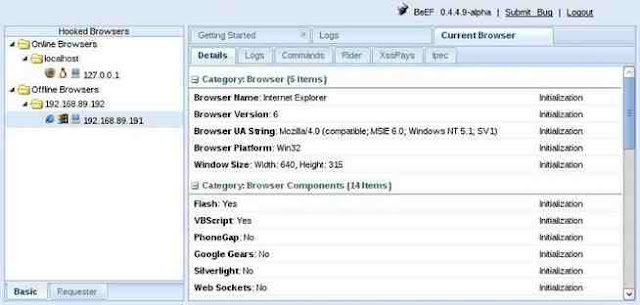
Step 4: Hooking a Browser
The key to success with BeEF is to “hook” a browser. This basically means that we need the victim to visit a vulnerable web app. This injected code in the “hooked” browser then responds to commands from the BeEF server. From there, we can do a number of malicious things on the victim’s computer.
BeEF has a JavaScript file called “hook.js,” and if we can get the victim to execute it in a vulnerable web app, we will hook their browser! In future tutorials, we will look at multiple ways to get the victim’s browser hooked.
In the screenshot below, I have “hooked” an Internet Explorer 6 browser on an old Windows XP on my LAN at IP 192.168.89.191.
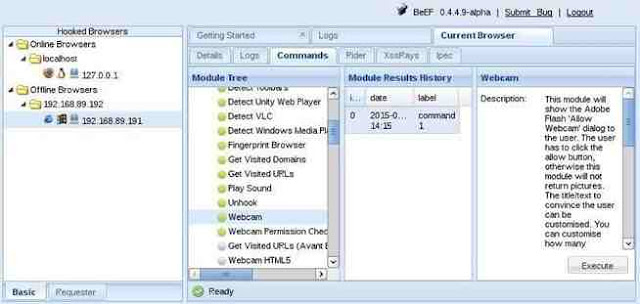
Step 5: Running Commands in the Browser
Now, that we have hooked the victim’s browser, we can use numerous built-in commands that can executed from the victim’s browser. Below are just a few examples; there are many others.
- Get Visited Domains
- Get Visited URLs
- Webcam
- Get All Cookies
- Grab Google Contacts
- Screenshot
In the screenshot below, I selected the “Webcam” command that many of you may be interested in. As you can see, when I execute this command, an Adobe Flash dialog box will pop up on the screen of the user asking, “Allow Webcam?” If they click “Allow,” it will begin to return pictures from the victim’s machine to you.
Of course, the text can be customized, so be imaginative. For instance, you could customize the button to say “You have just won the lottery! Click here to collect your winnings!” or “Your software is out of date. Click here to update and keep your computer secure.” Other such messages might entice the victim to click on the box.
Step 6: Getting Cookies
Once we have the browser hooked, there is almost unlimited possibilities of what we can do. If we wanted the cookies of the victim, we can go to “Chrome Extensions” and select “Get All Cookies” as shown in the screenshot below.

When we click on the “Execute” button to the bottom right, it will begin collecting all the cookies from the browser. Obviously, once you have the user’s cookies, you are likely to have access to their websites as well.
BeEF is an extraordinary and powerful tool for exploiting web browsers. In addition to what I have shown you here, it can also be used to leverage operating system attacks. We will be using it and other tools in my new series on hacking web applications, mobile devices, and Facebook, so keep coming back, my greenhorn hackers.
Recommended Articles To Become A Hacker:
How To Become A Hacker - Basic Guide For Beginners 2015
Understand The Hacker Mindset To Become A Real Hacker
Programming Languages For Hackers And Learn It From Most 6 Helpful Websites
Installing Hackers OS Kali Linux In VMware (Beginners Guide With Screenshots)
Easy Steps to Create Web Penetration Testing Lab in Kali Linux
Introduction to using Metasploit in Kali Linux
An Introduction To Hacker’s OS: Kali Linux And Setup Tutorial.
Linux Powerful Distros For Hacking Or Security: Kali, Tails And Qubes
Become A Hacker: What Is Denial of Service (DoS) Attack?
Available link for download
Subscribe to:
Posts (Atom)