Saturday, July 15, 2017
Kali Linux Tutorial How To Brute Force Wordpress Using Wpscan Tool
Kali Linux Tutorial How To Brute Force Wordpress Using Wpscan Tool

As a WordPress administrator or webmaster you are responsible for the security of the WordPress blog or website you manage. Most probably you’ve already done a lot to beef up the security and today we will show you how to brute force Wordpress password in Kali Linux using Wpscan to checking your Password Strength.
Disclaimer: This tutorial is for educational purposes only and we are NOT responsible in any way for how this information is used, use it at your own risk.
As we now WPScan is a black box WordPress vulnerability scanner, and it is installed by default in kali linux we will use it for brute forcing wordpress, If you have no idea about Kali Linux then i recommend you to read this article: An Introduction To Hacker’s OS: Kali Linux Setup Tutorial.
We will use our wordpress platform that we already installed in our kali linux. If you have not already done visit our article: Complete Guide To Setup Wordpress In Kali Linux With Xampp Server .
Letss start,
- Open your Kali Linux Terminal and start Xampp server by typing the following command:
root@kali: /opt/lampp/lampp start
- Now we need to Enumerate users, type in terminal:
root@kali: wpscan -u 127.0.0.1/wordpress --enumerate u
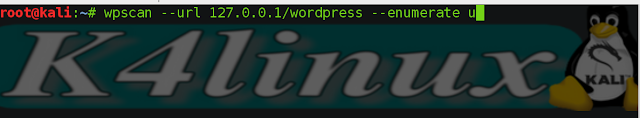
- Wpscan will automatically search the admin username.

- Now Do wordlist password brute force on the username, type in terminal:
root@kali: wpscan --url 127.0.0.1/wordpress --wordlist /root/pass --username k4linux
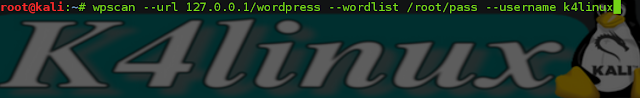
- --wordlist set the location of your Password Wordlist
- --username set the administrator username that you have found
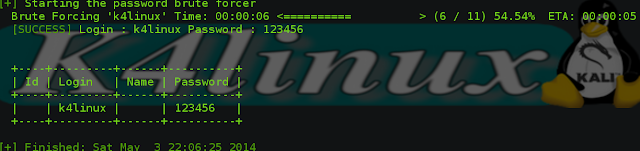
After a search Wpscan will find the password and this will take a few minutes, this depends on your Wordlist.
Efficiency of the Brute Force depend on how much strong is your wordlist and how many password contains it.
Watch the video tutorial for more explanation (Wpscan):
Recommended Hacking Tutorial:
- How to Hack Website Using Sql Map in Kali Linux - Sql Injection
- Kali Linux Tutorial: Find Vulnerabilities for Any Website Using Nikto
- Heartbleed Attack: Exploiting OpenSSL Vulnerability Using Metasploit
- Kali Linux Tutorial: Hack a Website login Page Password Using Wireshark
Available link for download
Kali Linux Tutorial How To Use Doona Bruteforce Exploit Detector Tool BED
Kali Linux Tutorial How To Use Doona Bruteforce Exploit Detector Tool BED

Doona is a fork of the Bruteforce Exploit Detector Tool (BED). BED is a program which is designed to check daemons for potential buffer overflows, format string bugs etc.
Doona is Australian for duvet. It adds a significant number of features/changes to BED. (Defination Kali.org)
If you haven’t install Doona just simply follow Commands:-
Apt-get updateApt-get install doona
How to use doona:-
1. Type “doona” and you will get option like show in figure below:-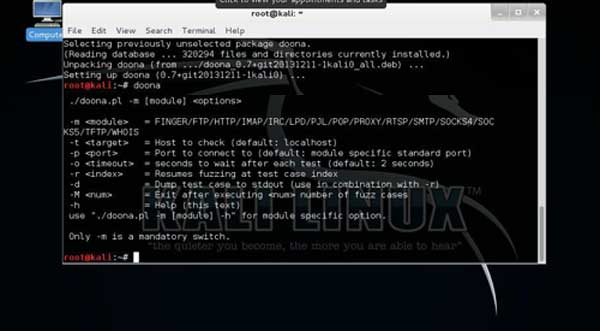 |
doona |
 |
Target ip |
Command:- doona -m http -t <target ip> -p <target port> -M 10 (max not after exit)
This is my command :- doona -m http -t 216.58.210.238 -M 10
 |
Command |
DOONA USAGE EXAMPLE
Use the HTTP plugin (-m HTTP) to fuzz the target (-t 192.168.1.15), stopping after 5 cases (-M 5):root@kali:~# doona -m HTTP -t 192.168.1.15 -M 5Doona 0.7 by Wireghoul (www.justanotherhacker.com) based on BED by mjm and snakebyte+ Buffer overflow testing
1/37 [XAXAX] ……
Max requests (5) completed, index: 5
Also Read:
- Easy Way To Crack Password Using John The Ripper In Kali Linux
- Practical Tutorial For Best 15 Pentest Tools In Kali Linux 2.0
- Kali Linux Tutorial: Finding Exploits Using the Searchsploit Tool
Available link for download
Wednesday, June 14, 2017
Kali Linux Tutorial Introduction To Parsero Vulnerability Analysis Tool
Kali Linux Tutorial Introduction To Parsero Vulnerability Analysis Tool
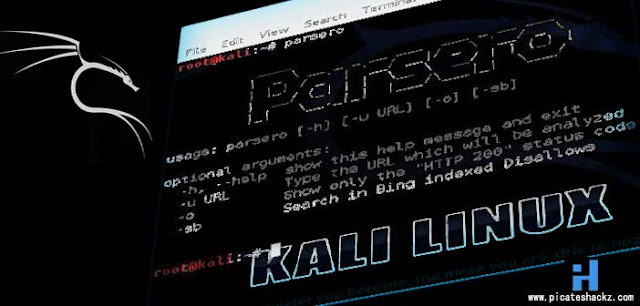
Parsero is a free script written in Python which reads the Robots.txt file of a web server and looks at the Disallow entries. The Disallow entries tell the search engines what directories or files hosted on a web server mustn’t be indexed. For example, “Disallow: /portal/login” means that the content on www.example.com/portal/login it’s not allowed to be indexed by crawlers like Google, Bing, Yahoo… This is the way the administrator have to not share sensitive or private information with the search engines.
But sometimes these paths typed in the Disallows entries are directly accessible by the users without using a search engine, just visiting the URL and the Path, and sometimes they are not available to be visited by anybody… Because it is really common that the administrators write a lot of Disallows and some of them are available and some of them are not, you can use Parsero in order to check the HTTP status code of each Disallow entry in order to check automatically if these directories are available or not.
Also, the fact the administrator write a robots.txt, it doesn’t mean that the files or directories typed in the Dissallow entries will not be indexed by Bing, Google, Yahoo… For this reason, Parsero is capable of searching in Bing to locate content indexed without the web administrator authorization. Parsero will check the HTTP status code in the same way for each Bing result.
- Recommended: An Introduction To Hacker’s OS: Kali Linux Setup Tutorial
TOOLS INCLUDED IN THE PARSERO PACKAGE:-
Open up a terminal in Kali Linux and type following command:root@kali:~# parsero -h

PARSERO USAGE EXAMPLE:-
root@kali:~# parsero -u www.bing.com -sb____
| _ __ _ _ __ ___ ___ _ __ ___
| |_) / _` | ‘__/ __|/ _ ‘__/ _
| __/ (_| | | __ __/ | | (_) |
|_| __,_|_| |___/___|_| ___/Starting Parsero v0.75 (https://github.com/behindthefirewalls/Parsero) at 06/09/14 12:48:25
Parsero scan report for www.bing.com
http://www.bing.com/travel/secure 301 Moved Permanently
http://www.bing.com/travel/flight/flightSearchAction 301 Moved Permanently
http://www.bing.com/travel/css 301 Moved Permanently
http://www.bing.com/results 404 Not Found
http://www.bing.com/spbasic 404 Not Found
http://www.bing.com/entities/search 302 Found
http://www.bing.com/translator/? 200 OK
http://www.bing.com/Proxy.ashx 404 Not Found
http://www.bing.com/images/search? 200 OK
http://www.bing.com/travel/hotel/hotelSearch 301 Moved Permanently
http://www.bing.com/static/ 404 Not Found
http://www.bing.com/offers/proxy/dealsserver/api/log 405 Method Not Allowed
http://www.bing.com/shenghuo 301 Moved Permanently
http://www.bing.com/widget/render 200 OK
Also Read:
- Kali Linux Tutorial: Find IP Address Of Any Website And Trace Its Location
- Kali Linux Tutorial: Information Gathering Using TheHarvester
- Kali Linux Tutorial: Using Maltego Tool To Scan Network And Finding IP
Available link for download
Monday, May 15, 2017
Kali Linux Tutorial Finding Exploits Using the Searchsploit Tool
Kali Linux Tutorial Finding Exploits Using the Searchsploit Tool

What is Vulnerability Exploit?
Words like "exploit" and "vulnerability" are tightly bound together. Often, a script/program will exploit a specific vulnerability. Since most vulnerabilities are exploited by script kiddies, the vulnerability is often known by the name of the most popular script that exploits it. In any case, there are broad-spectrum vulnerability scanners/assessment tools that will scan a system and look for common vulnerabilities. These are often used in order to toughen up a computer system.
In computer security, the term vulnerability is applied to a weakness in a system that allows an attacker to violate the integrity of that system. Vulnerabilities may result from weak passwords, software bugs, a computer virus or a script code injection, and a SQL injection.
Introduction
When we are looking for ways to hack a system, we need a specific exploit to take advantage of a certain vulnerability in the operating system, service, or application.
Remember, exploitation is very specific, there is no one silver bullet that will allow you to exploit all systems. You need to find an exploit that will specifically take advantage of a vulnerability in the system that you are attacking. That is where the Exploit Database (www.exploit-db.com) can be so incredibly useful.
EDB is a project of Offensive Security, the same folks who developed BackTrack and Kali Linux, which includes exploits categorized by platform, type, language, port, etc. to help you find the exploit that will work in your particular circumstance. Then, if you feel it will work on your target, you can simply copy and paste it into Kali for your attack.
Step 1: Fire Up Kali & Open a Browser
Lets start by firing up Kali and opening a browser, such as Iceweasel, the default browser in Kali (EDB can be reached from any browser, in any operating system). If we use the default browser in Kali, we can see that there is a built-in shortcut to the "Exploit-DB" in the browser shortcut bar, as seen below.
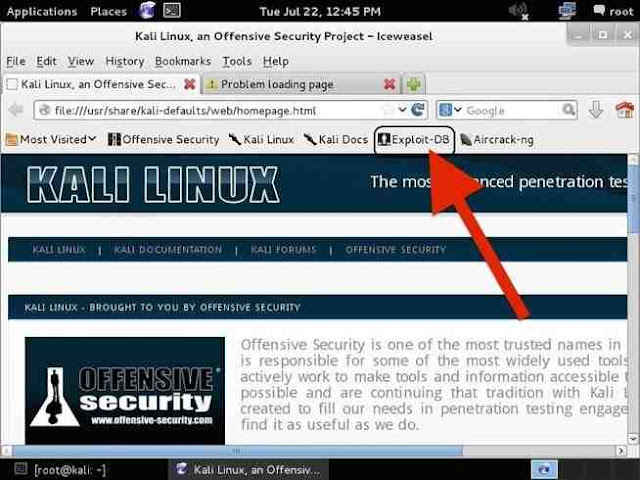
When we click on it, it takes us to the Exploit Database, as seen below.

If you are not using Iceweasel and its built-in shortcut, you can navigate to Exploit-DB by typing www.exploit-db.com in the URL bar.
Step 2: Search the Exploit Database
If we look at the top menu bar in the Exploit Database website, second from the right is a menu item called "Search". When we click on it, it enables us to search the database of exploits and returns a search function screen similar to the screenshot below.

Lets use this search function to find some recent Windows exploits (we are always looking for new Windows exploits, arent we?). In the search function window, we can enter any of the following information;
- Description
- Free Text Search
- Author
- Platform (this is the operating system)
- Type
- Language
- Port
- OSVDB (the Open Source Vulnerability Database)
- CVE (Common Vulnerability and Exploits)
The last two fields can be used if you are specifically looking for an exploit that takes advantage of a known, numbered vulnerability in either of those databases.
In the Platform field, enter "Windows", in the Type field, enter "remote", and in the Free Text Search box, enter "Office". When we do so, the Exploit Database returns a list and a link to all of the exploits that meet those criteria. Of course, you can put in whatever criteria you are searching for. I am only using these as an example.

Step 3: Open an Exploit
From the search results page, we can click on any of the two pages of search results and it will take us to the particular exploit. I clicked on the very first exploit in the list "Internet Explorer TextRange Use-After Free (MS14_012)". When I do so, I am brought to a screen that displays the exploit code like that below. I have circled the description in the code of the exploit.
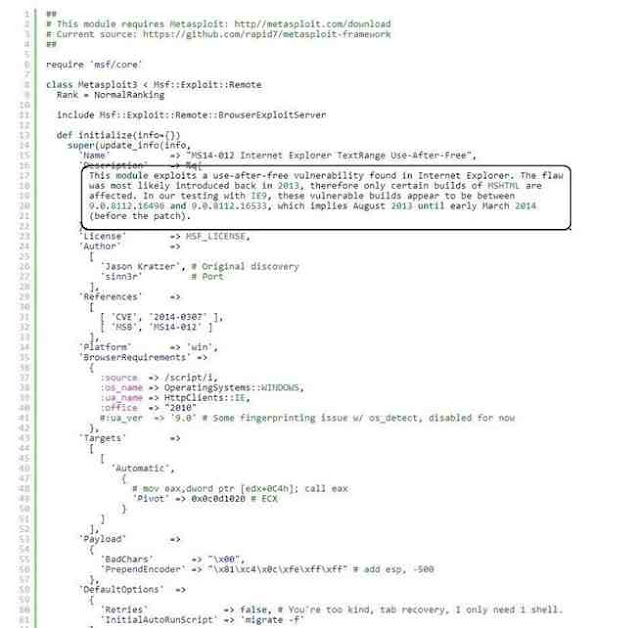
This exploit works against Internet Explorer that was built between August 2013 and March 2014. If you want to use it, you can simply copy and paste this text file and put it into the exploit directory in Metasploit (if you are using an up-to-date version of Metasploit, it is already included). This is a good example of how specific an exploit can be.
Step 4: Open Up Searchsploit
Kali, having also been developed by Offensive Security, has built into it a local database of exploits based on the same Exploit Database. We can access it by going to Applications -> Kali Linux -> Exploitation Tools -> Exploit Database and clicking on searchsploit as shown below.
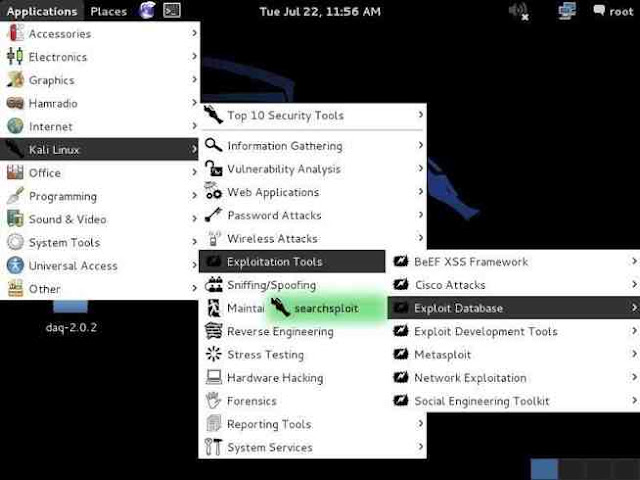
It will open a screen like that below that details the basic syntax on how to use searchsploit. Note that it explains that you must use lowercase search terms and that it searches a CSV (comma separated values) file from left to right, so search term order matters.
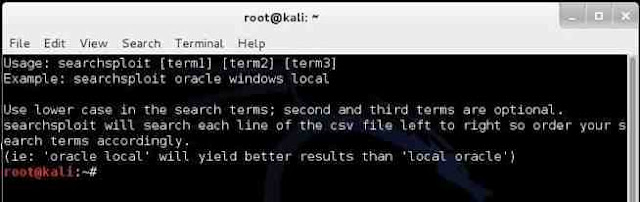
Step 5: Search the Exploit Database with Searchsploit
Now that we have opened a terminal for searchsploit, we can now use this tool to search our local copy of the Exploit Database. As you might expect, our local copy of the exploit database is much faster to search, but does NOT have all the updates that the online database does. Despite this, unless we looking for the very latest exploits, the local database works fast and is effective.
One other note on its use. As the information is organized in CSV files, searches locally often will yield results slightly differently than the online database. In the screenshot below, I searched for "Windows" and "Office" and only received a single result, unlike what I received when I used the online database.

Exploit Database is an excellent repository for exploits and other hacks that we might need, including new Google hacks, white papers on security and hacking, denial of service (DOS) attacks, and shellcode that you can use out the box or tailor for your unique attack.
How To Become A Hacker - Basic Guide For Beginners 2015
Understand The Hacker Mindset To Become A Real Hacker
Programming Languages For Hackers And Learn It From Most 6 Helpful Websites
Installing Hackers OS Kali Linux In VMware (Beginners Guide With Screenshots)
Easy Steps to Create Web Penetration Testing Lab in Kali Linux
Introduction to using Metasploit in Kali Linux
An Introduction To Hacker’s OS: Kali Linux And Setup Tutorial.
Linux Powerful Distros For Hacking Or Security: Kali, Tails And Qubes
Become A Hacker: What Is Denial of Service (DoS) Attack?
Available link for download
Saturday, April 15, 2017
King of Thieves Hack Cheat Tool
King of Thieves Hack Cheat Tool
Check King of Thieves Hack Proof and How to use
About King of Thieves Hack Cheat Tool
King of Thieves Hack Cheat Tool Features
-Unlimited Gold
-Unlimited Gems
-Unlimited Keys
-Android/iOS Operating System Supported
-Every Browser Supported
-Windows Vista/7/8 Supported
-Free to use for limited time
-Free check for new updates
-Tested every day for bugs and glitches
How to use King of Thieves Hack Cheat Tool
1. Download the program from the link bellow
2. Open your game in your browser/device and let it run. Also connect usb cable to your device if you’re using mobile devices.
3. Open the King of Thieves Hack Cheat Tool.
4. Select the desired amounts of Gold,Gems,Keys then click the “Start” button.
5. Press the home button on your device and then open the game again. Refresh the game if using browser.
6. Done ! Enjoy the game !
Screenshots
Statistics
Name: King of Thieves Hack Cheat Tool
Version: Latest
Size: 1.9 MB
Price: Free to download Limited Time
Total Downloads: 23629
Download
The hack requires the latest Microsoft .NET Framework to work. Click the button bellow to download if your application does not start.
Download King of Thieves Hack Cheat Tool from Zippyshare Free Download!
King of Thieves Hack Cheat Tool
Available link for download
Tuesday, April 11, 2017
Kali Linux Tutorial DDoS Attack Using GoldenEye Tool In Kali 2 0 Sana
Kali Linux Tutorial DDoS Attack Using GoldenEye Tool In Kali 2 0 Sana

Today we are going to talk about how to use GoldenEye to perform a ddos attack, if you want learn about ddos attack you just need to read the below recommended article about DDoS , and Here in this tutorial we will use GoldenEye Python based app in kali linux 2.0 as the Operating system.
Recommended:
- Become A Hacker: What Is Denial of Service (DoS) Attack?
- An Introduction To Hacker’s OS: Kali Linux Setup Tutorial
- Improved Features Of New Kali Linux 2.0 And How To Upgrade To It
Disclaimer: This tutorial is for educational purposes only and we are NOT responsible in any way for how this information is used, use it at your own risk.
What is GoldenEye ?
GoldenEye is an python app for SECURITY TESTING PURPOSES ONLY! And he is a HTTP DoS Test Tool.Dowloading GoldenEye :
To Download GoldenEye Go To : https://github.com/jseidl/GoldenEyeOre open your Terminal on KAli Linux 2.0 and follow:
- root@k4linux:~# git clone https://github.com/jseidl/GoldenEye.git
- Cloning into GoldenEye...
- remote: Counting objects: 70, done.
- remote: Total 70 (delta 0), reused 0 (delta 0), pack-reused 70
- Unpacking objects: 100% (70/70), done.
- Checking connectivity... done.
- root@k4linux:~# cd GoldenEye/
- root@k4linux:~/GoldenEye# ls
- goldeneye.py README.md res util
- root@k4linux:~/GoldenEye#
How To Use GoldenEye?
GoldenEye it simple to use after downloading it go to the folder where you saved them.Change the permission and make it executable :
root@k4linux:~/GoldenEye# chmod +x goldeneye.py
root@k4linux:~/GoldenEye# ./goldeneye.py [OPTIONS]
root@k4linux:~/GoldenEye# ./goldeneye.py -h
Watch the video tutorial for more explanation (GoldenEye):
If you have encountered a problem or you have any questions or remarks please feel free to set a comment.
Recommended Articles To Become Hacker:
- Become a Hacker: Best 20 Tips for Beginners to Start Learning
- Become a Hacker!, What does Exactly Mean by a Hacker ?
- The Reason Behind Why Hackers Using Linux As Their Primary OS
- Hacker Tips - 10 Common Mistakes You Should Avoid When Coding
- Become A Hacker: Top Books To Learn Ethical Hacking
- What You Should Do To Become A Hacker!
- Python For Hackers And Learn It From Top 5 Web Resources
- Become A Hacker: Types Of Cyber Attacks And Must Know Facts
- Become A Hacker: Learn the Basics of Networking
- Penetration Testing: Basic Guide For Beginners
- Understand The Hacker Mindset To Become A Real Hacker
- Programming Languages For Hackers And Learn It From Most 6 Helpful Websites
- How To Become A Hacker - Basic Guide For Beginners
Available link for download
Saturday, April 8, 2017
Kali Linux Tutorial Introduction To ShellNoob Exploitation Tool
Kali Linux Tutorial Introduction To ShellNoob Exploitation Tool

Writing shellcodes has always been super fun, but some parts are extremely boring and error prone. Focus only on the fun part, and use ShellNoob!
Features:-
- convert shellcode between different formats and sources. Formats currently supported: asm, bin, hex, obj, exe, C, python, ruby, pretty, safeasm, completec, shellstorm. (All details in the “Formats description” section.)
- interactive asm-to-opcode conversion (and viceversa) mode. This is useful when you cannot use specific bytes in the shellcode and you want to figure out if a specific assembly instruction will cause problems.
- support for both ATT & Intel syntax. Check the –intel switch.
- support for 32 and 64 bits (when playing on x86_64 machine). Check the –64 switch.
- resolve syscall numbers, constants, and error numbers (now implemented for real! :-)).
- portable and easily deployable (it only relies on gcc/as/objdump and python). It is just one self-contained python script, and it supports both Python2.7+ and Python3+.
- in-place development: you run ShellNoob directly on the target architecture!
- built-in support for Linux/x86, Linux/x86_64, Linux/ARM, FreeBSD/x86, FreeBSD/x86_64.
- “prepend breakpoint” option. Check the -c switch.
- read from stdin / write to stdout support (use “-” as filename)
- uber cheap debugging: check the –to-strace and –to-gdb option!
- Use ShellNoob as a Python module in your scripts! Check the “ShellNoob as a library” section.
- Verbose mode shows the low-level steps of the conversion: useful to debug / understand / learn!
- Extra plugins: binary patching made easy with the –file-patch, –vm-patch, –fork-nopper options! (all details below)
download from :- https://github.com/reyammer/shellnoob
Also Read:
- Easy Way To Crack Password Using John The Ripper In Kali Linux
- Kali Linux Tutorial: Setting Up ProxyChains + Tor For Anonymity And Security
- Kali Linux Tutorial: Introduction To Parsero Vulnerability Analysis Tool
TOOLS INCLUDED IN THE SHELLNOOB PACKAGE
- root@kali:~# shellnoob -h
- shellnoob.py [–from-INPUT] (input_file_path | – ) [–to-OUTPUT] [output_file_path | – ]
- shellnoob.py -c (prepend a breakpoint (Warning: only few platforms/OS are supported!)
- shellnoob.py –64 (64 bits mode, default: 32 bits)
- shellnoob.py –intel (intel syntax mode, default: att)
- shellnoob.py -q (quite mode)
- shellnoob.py -v (or -vv, -vvv)
- shellnoob.py –to-strace (compiles it & run strace)
- shellnoob.py –to-gdb (compiles it & run gdb & set breakpoint on entrypoint)
- Standalone “plugins”
- shellnoob.py -i [–to-asm | –to-opcode ] (for interactive mode)
- shellnoob.py –get-const <const>
- shellnoob.py –get-sysnum <sysnum>
- shellnoob.py –get-strerror <errno>
- shellnoob.py –file-patch <exe_fp> <file_offset> <data> (in hex). (Warning: tested only on x86/x86_64)
- shellnoob.py –vm-patch <exe_fp> <vm_address> <data> (in hex). (Warning: tested only on x86/x86_64)
- shellnoob.py –fork-nopper <exe_fp> (this nops out the calls to fork(). Warning: tested only on x86/x86_64)
- “Installation”
- shellnoob.py –install [–force] (this just copies the script in a convinient position)
- shellnoob.py –uninstall [–force]
- Supported INPUT format: asm, obj, bin, hex, c, shellstorm
- Supported OUTPUT format: asm, obj, exe, bin, hex, c, completec, python, bash, ruby, pretty, safeasm
- All combinations from INPUT to OUTPUT are supported!
- Check out the README file for more info.
SHELLNOOB USAGE EXAMPLE:-
Start in interactive mode (-i) in asm to opcode mode (–to-opcode):
- root@kali:~# shellnoob -i –to-opcode
- asm_to_opcode selected (type “quit” or ^C to end)
- >> xchg %eax, %esp
- xchg %eax, %esp ~> 94
- >> ret
- ret ~> c3
- >>
Available link for download
Saturday, March 4, 2017
Kiwi Wonderland Hack Cheat Tool
Kiwi Wonderland Hack Cheat Tool
Check Kiwi Wonderland Hack Proof and How to use
About Kiwi Wonderland Hack Cheat Tool
So you want to know how to hack Kiwi Wonderland right? We did it for you and created Kiwi Wonderland Hack Cheat Tool. It’s the perfect application for those people who want some nice and easy cheats that can be used fast and safe.
Add more Lives,Coins very simple and effortless using the implemented Kiwi Wonderland Cheats. Our team coded the tool based on the glitches found in game script files. This application can be used for Android and iOS also for Facebook if the game is available there. The similarities between the systems where can be used makes it very easy to implement it everywhere.
Now is very easy to upgrade those premium items for free using Kiwi Wonderland Hack Cheat Tool and add Unlimited Lives,Coins in your account. How do you think you’ll play the game when you have everything that you want? I think you will enjoy it more and more and you’ll be happy with the help provided by Kiwi Wonderland Hack.
You now have the opportunity to get it for free. Such a powerful application and don’t have to pay anything you will wonder? Yes that’s true. Get it from Zippyshare or Dropbox now and enjoy the greatness of Kiwi Wonderland Hack Cheat Tool.
Kiwi Wonderland Hack Cheat Tool Features
-Unlimited Lives
-Unlimited Coins
-Android/iOS Operating System Supported
-Every Browser Supported
-Windows Vista/7/8 Supported
-Free to use for limited time
-Free check for new updates
-Tested every day for bugs and glitches
How to use Kiwi Wonderland Hack Cheat Tool
1. Download the program from the link bellow
2. Open your game in your browser/device and let it run. Also connect usb cable to your device if you’re using mobile devices.
3. Open the Kiwi Wonderland Hack Cheat Tool.
4. Select the desired amounts of Lives,Coins then click the “Start” button.
5. Press the home button on your device and then open the game again. Refresh the game if using browser.
6. Done ! Enjoy the game !
Screenshots
Statistics
Name: Kiwi Wonderland Hack Cheat Tool
Version: Latest
Size: 1.9 MB
Price: Free to download Limited Time
Total Downloads: 20365
Download
The hack requires the latest Microsoft .NET Framework to work. Click the button bellow to download if your application does not start.
Download Kiwi Wonderland Hack Cheat Tool from Zippyshare Free Download!
Incoming search terms:
- kiwi wondarland cheat code
- kiwi wonderland download
- Kiwi Wonderland Hack Cheat Tool
Kiwi Wonderland Hack Cheat Tool
Available link for download
Sunday, February 26, 2017
Kali Linux Tutorial Using Maltego Tool To Scan Network And Finding IP
Kali Linux Tutorial Using Maltego Tool To Scan Network And Finding IP

Using Maltego in Kali to Recon a Target Network
Step 1: Open Maltego & Register
Let’s start by firing up Kali and then opening Maltego. Here is a complete tutorial about hackers OS Kali Linux, so read this before you go ahead: An Introduction To Hacker’s OS: Kali Linux Setup Tutorial
When you open Maltego, you will need to wait a brief moment for it to startup. After it finishes loading, you will be greeted by a screen asking you to register Maltego.
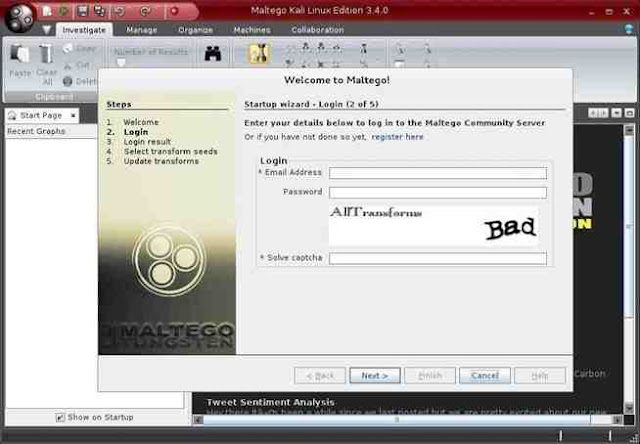
Go ahead and register and save and remember your password as you will need it again the next time you login into Maltego.
Step 2: Choose a Machine & Parameters
After successfully registering and logging into Maltego, we will have to decide what type of “machine” we want to run against our target. In Maltego’s parlance, a machine is simply what type of footprinting we want to do against our target. Here, we are focusing on the network footprinting, so our choices are:
- Company Stalker (this gathers email information)
- Footprint L1 (basic information gathering)
- Footprint L2 (moderate amount of information gathering)
- Footprint L3 (intense and the most complete information gathering)
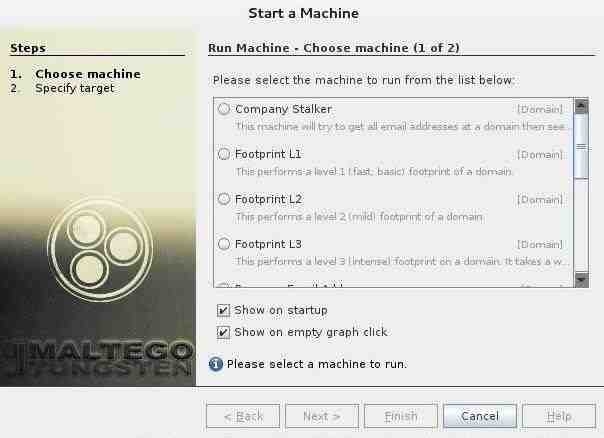
Step 3: Choose a Target
Now, that we have chosen a type of machine for our footprinting, we will need to choose a target. Let’s choose our friends at SANS, one of the leading IT security training and consulting firms in the world.
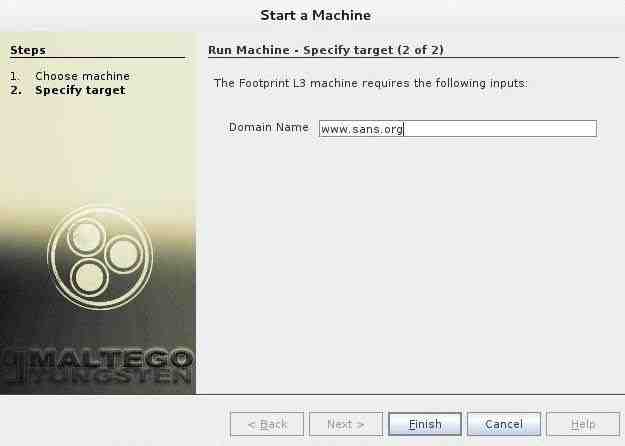
Now, click “Finish” and let Maltego do its work.
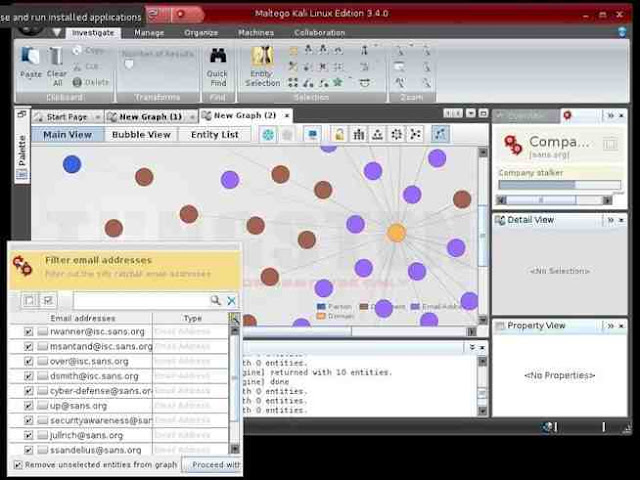
Step 4: Results
Maltego will now begin to gather info on our target domain, sans.org, and display it on screen. In the screenshot below, we can see that Maltego has already collected the email addresses from the site, while it collects the nameservers and mail servers.
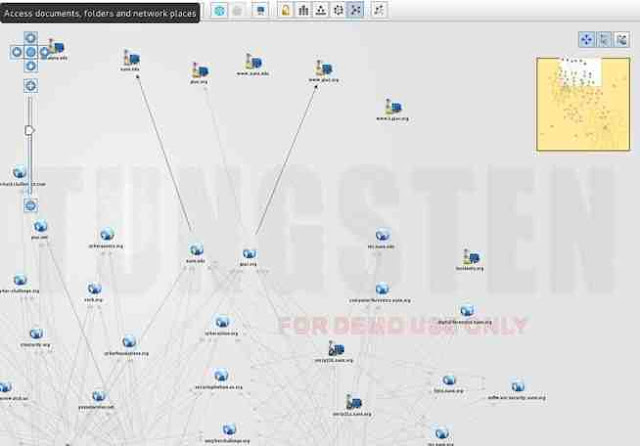
Finally, we can click on “Bubble View” when Maltego is done and see all of the relationships between our target and its subdomains and linked sites.
How to find IP address

By clicking left button of mouse drag the domain in Main view.
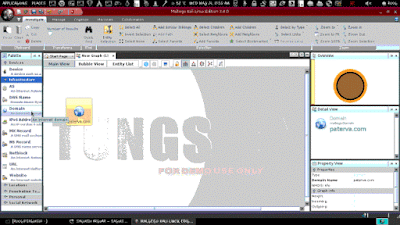
Double click on domain icon and rename it into your target domain. Here I am taking google.com as example.
Here we are searching for top level domain for our target domain. First right click on domain then
Run Transform ? All Transforms ? To Domain ( Find other TLDs)
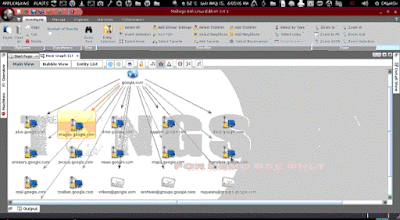
Here we got the result of TLD search.
Now we are to gain more information about these domains. First of all select all domains by dragging left mouse button or you can select one by one press Shift + left click.
After selecting all domains, right click one of them and then
Run Transform ? All Transforms ? To Website (Quick-Lookup)
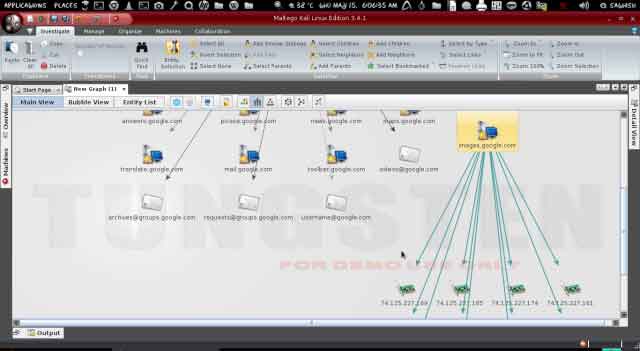
Here we are going to search all website which are associate with these domains.
Well here we are just replacing the a website icon I have targeted http://www.google.com for more info follow the image. This is not a necessary part but you should learn it.
Here we are going to find the IP address of our target website. Right click on target website then
Run Transform ? Resolve to IP ? To IP Address (DNS)
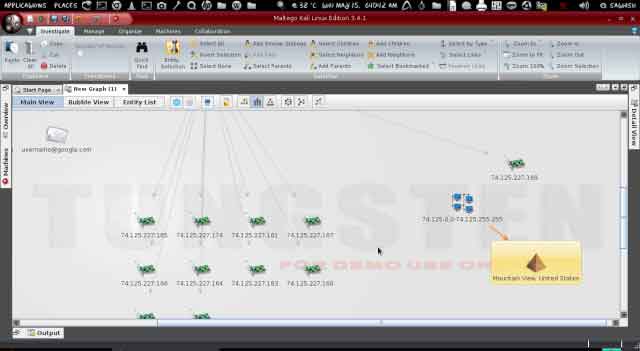
Here we got the IP address of our target website and the detail of where its located.
Conclusion
Maltego is an excellent tool to do network recon on our potential target, enabling us to do numerous types of recon in a single scan with a single tool. Maltego is also capable of doing individual recon, but we will leave that for my next Maltego article, see you my grey hats.Recommended Kali Linux Tutorials
- Kali Linux Tutorial: Hack A Web Browser Using BeEF
- Kali Linux Tutorial: How To Perform Evil Twin Wireless Access
- Kali Linux Tutorial: Hack a Website login Page Password Using Wireshark
- Kali Linux Tutorial: Finding Exploits Using the Searchsploit Tool
Available link for download